What Are Basic Web Hosting Best Practices
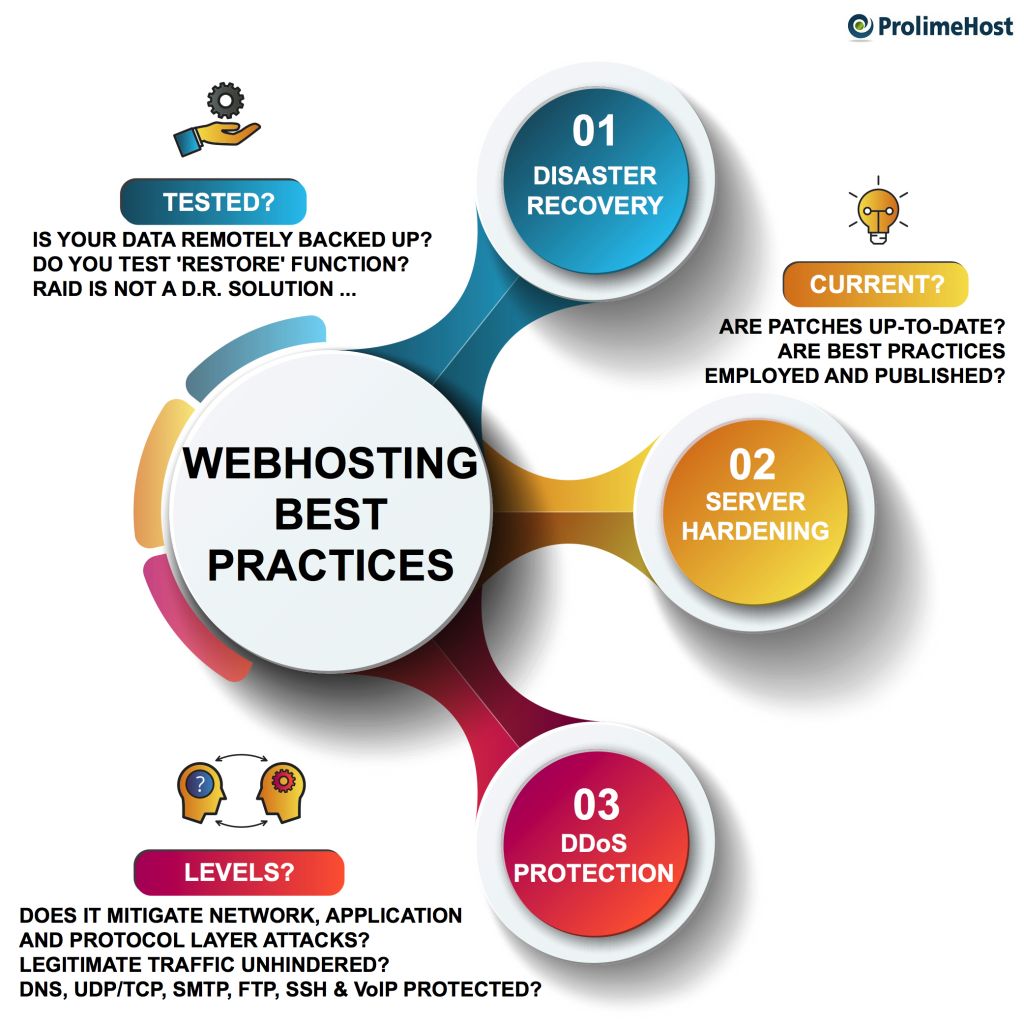
Best practices are defined as “procedures that have been shown by research and experience to produce optimal results and that is established or proposed as a standard suitable for widespread adoption.” Web hosting best practices should include disaster recovery, server hardening, DDoS protection, backups and updating patches.
Disaster Recovery
Way too many web hosting clients continue to view RAID configurations as disaster recovery solutions. While different RAID levels do address redundancy and performance factors, they are NOT disaster recovery solutions. Murphy’s Law says that if anything can go wrong, it will go wrong – and at the most inopportune time.
The key to effective disaster recovery solutions is backing up your mission critical data REMOTELY and then testing the restore function to ensure that you’ll be able to bring everything back up in a timely fashion.
Server Hardening
According to the Massachusetts Institute of Technology, “By not applying a patch you might be leaving the door open for a malware attack. Malware exploits flaws in a system in order to do its work. In addition, the time-frame between an exploit and when a patch is released is continually getting shorter.
Defects in clients like web browsers, email programs, image viewers, instant messaging software, and media players may allow malicious websites, etc. to infect or compromise your computer with no action on your part other than viewing or listening to the website, message, or media.”
How would you know if your web hosting provider employs best security practices when hardening your server? At a minimum the base install of all OS and post-OS software should come from a trusted source and that includes being connected to a completely trusted network. Each base install should also include all current service packs and patches.
DDoS Protection
In web hosting, ensuring that your servers and websites are protected from DDoS attacks is critically important as attacks by cybercriminals continues to increase in both scope and volume. An alarming number of web hosting providers still lack adequate DDoS protection services, so it’s incumbent to ask what protection they do provide.
If you’ve purchased DDoS protection from your web hosting provider, do you know what levels of network, application or protocol layers that it protects you from? When they filter attacks, will they allow legitimate traffic to pass through unhindered? Will those services encapsulate DNS, UDP/TCP, SMTP, FTP, SSH and VoIP protections?
BROUGHT TO YOU BY PROLIMEHOST
We’ve been in the web hosting industry for over a decade, helping hundreds of clients succeed in what they do best and that’s running their business. We specialize in Virtual Private Servers (VPS) and dedicated servers, with data centers in Los Angeles, Denver & Singapore.
VPS SERVICES: LIGHTNING FAST SSD VIRTUAL SERVERS
Our Virtual Private Servers all feature high performance Xeon processors and SSD storage in a RAID10 configuration to optimize your server’s performance, which dramatically enhances visitor experiences on your site.
That speed is backed by unparalleled 24/7 support, featuring both outstanding response AND resolution times to maximize your uptime.
Now is the time to join the ProlimeHost virtual private server revolution.
DEDICATED SERVERS: BACKED BY A 99.9% SLA NETWORK UPTIME GUARANTEE
We only use enterprise-class hardware in our dedicated servers and offer a four (4) hour hardware replacement. Throw in IPMI for remote management, support for public and private networks, free operating system (OS) re-installs, and SATA, SAS & SSD (including NVMe) storage. Call 1-877-477-9454 or contact us. For everything from gaming servers to cheap dedicated servers, we’re here to help.
ASIA OPTIMIZED SERVERS: IMPROVING CONNECTION SPEED AND QUALITY
Procuring an Asia optimized server improves the connection speed and quality between the server and the users in Asia or China. This can reduce latency, packet loss, jitter, and bandwidth issues that can affect the performance and reliability of the server and the applications hosted on it. For more information, please call 1-877-477-9454 or contact us.
- Software Versus Hardware RAID Solutions - July 26, 2024
- Why You Should Opt for a Dedicated Server at a Data Center - July 25, 2024
- Dedicated Server or VPS? Which is better? - July 24, 2024




